From basic phone calls to texting to downloading files and sending sensitive emails, there’s a lot happening on your device. But beyond the dangers of radiation and built-in Wi-Fi, cell phones pose more than health risks. Unfortunately, there are hackers out there with an interest in your personal information. Here’s how to tell whether you’re under surveillance and how you can secure your digital privacy.
Symptoms of Cell Phone Spying
It can be challenging to discover cell phone spying unless you know what to look for. Worse still, some cell phone symptoms may seem reasonable due to system speed or other factors, causing users to assume their device is failing. Here’s what to look for if you suspect cell phone spying.
Data Usage Spikes
All apps that connect to the internet have the potential to drive up your data usage. However, your favorite music or social media apps aren’t the only ones that can cause a data spike. Spy apps can use data to send and receive information on your phone without your permission, increasing your security risk and your phone bill.
Buy Book The Future of Foreign Intelligence: Privacy and Surveillance in a Digital Age (Inalienable Rights)
Illicit Activity
If your phone appears to be performing functions when you’re not using it, that’s another sign of spying. Lighting up or making noises while in standby mode could indicate an underlying hacking problem. These issues may also drain your battery, another common symptom of cell phone spying.
Power Glitches
While cell phones do have a limited lifespan, if your newer device is abruptly powering down and back on, someone may be accessing it remotely. Unfortunately, if a hacker can remotely power down your phone, odds are they can also access other functions.
Audio Interference
Similar to a landline, today’s cell phones are susceptible to hacking. You may hear clicking or beeping noises during an otherwise stable phone call. If so, that can indicate that someone is listening in. Another telltale sign that you have another set of ears on the line is background noise or additional voices.
Coded Texts
Nearly everyone receives junk text messages with lottery winning claims or unbelievable sales prices. But some text messages are hardly legible, including odd characters or codes. Low-quality spying software uses coding language to influence your device remotely. However, these texts can signal a malfunction in the software, which is still bad news for your cell phone.
Buy Book No Place to Hide: Edward Snowden, the NSA, and the U.S. Surveillance State
Low Battery
If you rarely charge your device but suddenly notice a drop in battery life, you may have a spy app running in the background. Even if it appears that all apps are off, an underlying spyware app could be draining your battery as it communicates with hackers. At the same time, the amount of memory it takes to run the app in the background can cause other cell phone processes to slow down.
Long Processes
Apart from glitching and slowing of standard cell phone functions, a cell phone that takes a long time to shut down could be carrying spyware. Similarly, difficulty getting the phone to begin its shutdown sequence can signify the presence of spyware, since attackers will want to keep the device on for constant monitoring.
On its own, any one of these symptoms may not seem like cause for alarm. But together, multiple symptoms may mean your phone has become compromised. So what’s the next step?
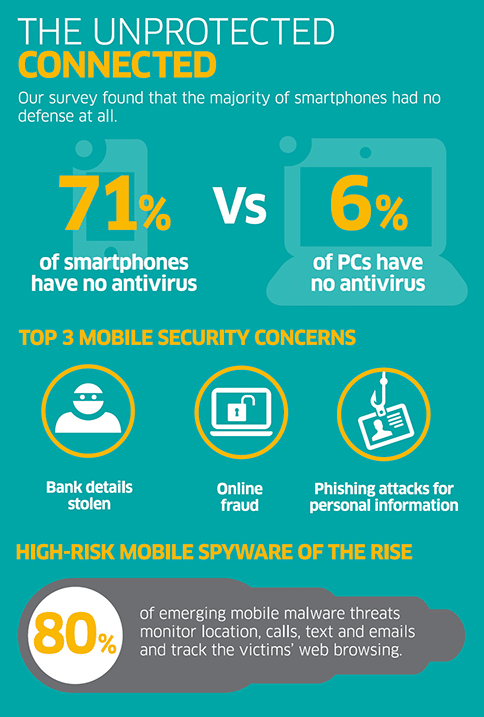
(http://www.valicomcorp.com/blog/2015/2/2/mobile-security-considerations-infographic)
How to Keep Your Cell Phone Secure
Keeping your mobile phone secure requires more than a lock-screen password or pattern. Although that may stop someone from picking up your device and gaining entry, remote hackers are far more advanced than nosy strangers or family members.
Privacy Precautions
Starting with the basics can help prevent spyware before any hacking attempts. Forbes suggests enacting these four steps as precautions against spyware infiltration.
Update Often
Most devices prompt users to download updates automatically. But you may not want to put your phone down long enough for it to complete an upgrade. Still, updating your phone often can protect against security breaches as software changes.
Cleanup Apps
If you have apps on your device that you don’t often use, clearing them out can keep hackers from finding a way in. If you never use an app, it’s not only taking up space but also leaving a door open for infiltration.
Auto-Lock
An auto-lock that’s password-protected is the first step in device security. While most hackers work remotely, someone could still pick up your phone and install malware or steal information if it’s unlocked.
Be Wi-Fi Wary
Using public Wi-Fi is always a potential risk to your security, so avoiding online shopping or logging into secure websites while you’re out is a smart idea. If you find yourself unable to avoid this in daily life, consider investing in a cheap VPN.
Buy Orgonite Cell Phone Protector (Helps Negate Harmful Radiation)
Already Being Spied On?
If you’re already experiencing troubling signs of spyware, the first step is to search for apps that may be acting on your device. Steps to finding and deleting apps will vary with each platform, but you can search for files that include terms like spy, monitor, track, stealth, or trojan.
If you find any files with these terms, you can act to delete them before they cause further harm. However, if you have already experienced all the symptoms listed above and tried removing illicit apps, your only remaining option may be a factory reset.
A factory reset deletes all third-party apps, so it removes harmful apps as well as all your favorites. Factory resetting also clears out your personal data like contacts, photos, and other files, so backing up critical files is a first step before resetting your device.
Buy Electro Smog Protection Products
About the Author
PixelPrivacy.com is all about making the world of online security accessible to everyone. We pride ourself in writing guides that we’re certain even our own mothers could understand! Be sure to head over to our blog if you’re interested in keeping your private information just that: Private!
Like our work? Support this site with a contribution via Paypal, cryptocurrencies, or P
This article appeared first on Stillness in the Storm.
This article (Is My Phone Being Spied On?) originally appeared on StillnessintheStorm.com and is free and open source. You have permission to share or republish this article in full so long as attribution to the author and stillnessinthestorm.com
Stillness in the Storm Editor’s note: Did you find a spelling error or grammar mistake? Send an email to [email protected], with the error and suggested correction, along with the headline and url. Do you think this article needs an update? Or do you just have some feedback? Send us an email at [email protected]. Thank you for reading.
Source:

Leave a Reply