() Recently, after WhatsApp updated its terms of use and privacy policy users have been migrating to other social media and messaging platforms due to concerns of their privacy.
by January 11th, 2021
However, what is not being reported by media is that CIA has developed tools which can hack not just WhatsApp, but bypass the encryption of,
- Signal
- Telegram
- Wiebo
- Confide
- Cloackman,
…by hacking your smartphones itself.
On March 7th, 2017, Wikileaks released a giant file of 8,761 documents from the U.S. Central Intelligence Agency (CIA) codenamed,
Wikileaks called the leak the first full part of the series “Year Zero”. The documents were stolen from a network that supposedly was “isolated” within the CIA itself.
The files include details on CIA’s software capabilities, such as the ability to compromise,
- cars
- smart TVs
- web browsers
- the operating systems of most smartphones
- other operating systems such as Microsoft Windows, macOS, and Linux…
A CIA internal audit identified 91 malware tools out of more than 500 tools in use in 2016 being compromised by the release.
The leaks outlined how the CIA could pretty much hack into any device with a suite of tools designed to read and copy data from electronic devices.
The documents detailed how, for example, authorities found a way to bypass encryption in a host of secure messaging apps such as WhatsApp and Telegram…
The CIA’s covert hacking division, had found a way to bypass vastly popular end-to-end encryption apps used on phones to prevent hacking and spying.
This was accomplished by hacking the smartphone first.
The code would run in the background and collect audio and text message traffic before encryption was applied through the apps.
What this means is that apps like,
- Signal
- Telegram,
…hugely popular because of their security features – were vulnerable.
People using these apps could still be spied on by the CIA.
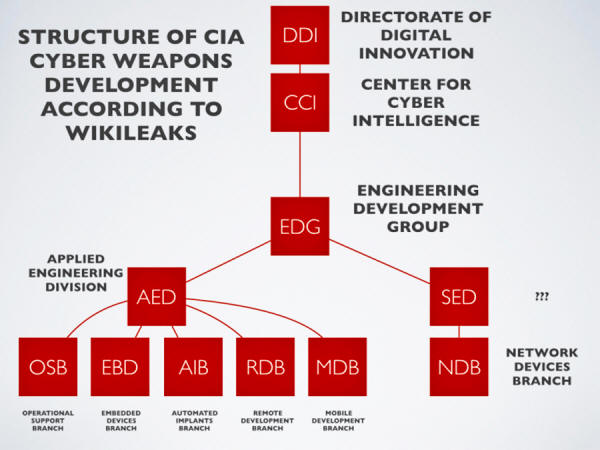
By the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5,000 registered users and had produced more than a thousand,
- hacking systems
- trojans
- viruses,
…and other ‘weaponized’ malware.
These techniques permit the CIA to bypass the encryption of WhatsApp, Signal, Telegram, Wiebo, Confide and Cloackman by hacking the “smart” phones that they run on and collecting audio and message traffic before encryption is applied.
According to WikiLeaks, once an Android smartphone is penetrated CIA can collect,
“audio and message traffic before encryption is applied”.
Some of CIA’s software is reportedly able to gain access to messages sent by instant messaging services.
This method of accessing messages differs from obtaining access by decrypting an already encrypted message.
While the encryption of messengers that offer end-to-end encryption, such as Telegram, WhatsApp and Signal, wasn’t reported to be cracked, their encryption can be bypassed by capturing input before their encryption is applied, by methods such as keylogging and recording the touch input from the user.
Stillness in the Storm Editor: Why did we post this?
The news is important to all people because it is where we come to know new things about the world, which leads to the development of more life goals that lead to life wisdom. The news also serves as a social connection tool, as we tend to relate to those who know about and believe the things we do. With the power of an open truth-seeking mind in hand, the individual can grow wise and the collective can prosper.
– Justin
Not sure how to make sense of this? Want to learn how to discern like a pro? Read this essential guide to discernment, analysis of claims, and understanding the truth in a world of deception: 4 Key Steps of Discernment – Advanced Truth-Seeking Tools.
Stillness in the Storm Editor’s note: Did you find a spelling error or grammatical mistake? Send an email to [email protected], with the error and suggested correction, along with the headline and url. Do you think this article needs an update? Or do you just have some feedback? Send us an email at [email protected]. Thank you for reading.
Source:
https://www.bibliotecapleyades.net/sociopolitica2/sociopol_cia48.htm

Leave a Reply